Network Planning Proposal
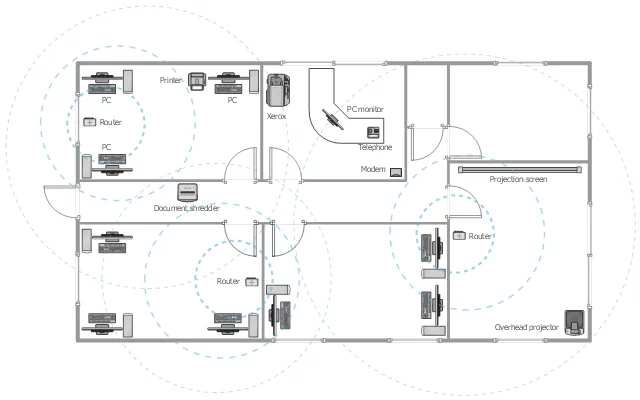
The fundamental motivation behind why we have to introduce and utilize a WLAN is because we should have the capacity to effortlessly get to the majority of the data that we require when we require it. The arrival of a venture with this WLAN comes as not paying for physical ropes and links to join and associate the more significant part of the PCs utilizing the framework. With the design being what it is an “L” shape, ensuring everybody can interface well could represent an issue (Jake, 2018). Likewise, with the nourishment court towards the base of the L form, we should actualize an answer that is able to take a decent flag in that region. The additional territory of apprehension will be the meeting area and history custody zones. We will again need to actualize an answer for increment scope through that territory too.
W/L System Facts
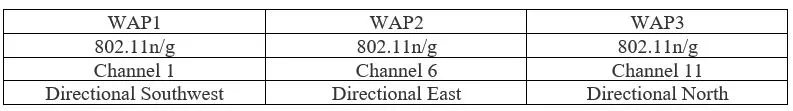
The remote framework I picked for this condition is 802.11n/g with the capability to use also 2.4 GHz or 5 GHz. The inspiration driving why I did this, is to have the ability to use contraptions that assistance 2.4 GHz like more settled apparatus and have the 5Ghz too for additional a la mode outfit and can have the ability to broaden if new rigging is incorporated. I have 3 Wireless Application protocols get to centers. I am undertaking this as of the L condition of the working environment domain. Every WAP is established to use varied 2.4 GHz or 5 GHz contingent after that type of contraption is the partner with the framework. I get a kick out of the chance to use directional receiving wires so we won’t have a massive amount of coverage and have more grounded signs to move beyond the dividers inside the working and furthermore including the banner stay inside the construction and not have the flag accessible outdoor the structure. I am consuming stations 2,5 and 10 with the objective that method I can incorporate more APs if essential unmistakable networks and I won’t have to pressure such an incredible sum over covering. With a similar number of dividers in this workplace, I expected to usage an AP with a more grounded banner to have the ability to have low clatter and protection. It is furthermore a noteworthy locale gathering area and lunchroom which can be an issue when attempting to interface from these zones and every side of the work environment, this is the reason I realized 3 APs have the ability to cover the entire office zone without any issues. I to a high degree required an alternate AP to close the zone with each one of the workspaces so way they won’t intrude with some other bit of the work environment, notwithstanding if there are subjects we can manage it an agreeable fact.
Complex Structure Safety
All ACME information will be safe. The information to be acquired will be client tags and keywords, account data for representatives, and additionally for clients. Client account data to be achieved are addresses and names, telephone numbers, and any financial data. Other information to be obtained will incorporate anything administration considers fit to be far as information utilized for organization devotions, counting illustrations, particulars et cetera (Kramer, 2018)s. This will incorporate and data All entrance focuses will have been straddling great off the floors so getting to them will be perceptible. All entrance focuses will utilize WPA-PSK encryption. The organizer will run a Cisco Network Management to have the capacity to deal with all entrance focuses and who can develop to these focuses and which sort of gadgets will have the capacity to entrance and utilize the system.
Just the MAC locations of the organization’s gear will be permitted to get into the system unless determined by the administration. If administration esteems other equipment to be allowed, at that point such changes will be made to suit. Every client will be given a client name and secret word to get to the system. In the end when every representative receives their username and secret word, they will have a bundle given to them that they should read and close down understanding that they comprehend the safety efforts and what to do if there is an issue. Once a month there ought to be a gathering with every one of the representatives managing the system, to go over safety techniques and conventions for everything which occur however at the workplace, including what they ought to do in the event that they think they have been traded off or on the off chance that they accidentally got to data they might not have approached as well. The system head and administration will likewise have their particular separate gatherings for any episodes and what the conventions are for upper administration occurrences.